- Category Business
- Version3.448.0
- Downloads 1.00M
- Content Rating Everyone
An Introduction to Protection 360™: Your Digital Shield in a Busy World
Protection 360™ is a comprehensive cybersecurity application designed to safeguard individual and corporate digital environments. Developed by CyberSecure Innovations, this tool combines real-time threat detection, data privacy management, and collaborative security features tailored for the modern digital user. Its primary strengths lie in its proactive threat monitoring, seamless team collaboration capabilities, and user-friendly interface, making it a compelling choice for professionals seeking robust protection without the hassle.
Core Features That Make Protection 360™ Stand Out
Real-Time Threat Monitoring and Automated Response
Imagine having an attentive security guard watching over your digital assets around the clock — that's exactly what Protection 360™ offers. Its real-time scanning engine actively detects malware, phishing attempts, and unauthorized access, providing instant alerts and automated countermeasures. This ensures that threats are mitigated before they can cause any damage, allowing users to operate with peace of mind.
Collaborative Security Workspaces
One of the app’s flagship features is its ability to facilitate collaborative work while maintaining high-security standards. Teams can create shared secure workspaces where members can collaboratively review, comment, and handle sensitive files without risking data leaks. This feature transforms traditional siloed security tools into an integrated environment that promotes teamwork without compromising safety.
Intuitive Data Privacy Management
Protection 360™ doesn’t just stop at threat detection; it prioritizes user privacy management. Its dashboard offers clear insights and controls over data access permissions, encryption protocols, and audit logs. Whether you're an individual user or managing a team, configuring privacy settings is straightforward, resembling managing a personalized vault that adjusts to your security needs.
User Experience: Seamless, Intuitive, and User-Centric
From the moment you open Protection 360™, it feels like stepping into a well-organized control center — clean, minimal, and thoughtfully designed. The interface employs a dark-themed, dashboard layout that’s easy on the eyes, even during prolonged sessions. Navigating through threat logs, collaborative tools, and privacy settings is intuitive, thanks to logical grouping and straightforward icons. The app's responsiveness is commendable; transitions are smooth, and features load swiftly, making the entire experience pleasant rather than burdensome.
Deep Dive into Core Functionalities
Threat Detection – A Digital Sentinel
The threat detection engine is powered by sophisticated algorithms that scan for vulnerabilities constantly. Unlike some competitors that rely solely on signature-based detection, Protection 360™ employs behavioral analysis, ensuring that emerging threats, zero-day exploits, and sophisticated phishing attacks are flagged early. For users, this translates into proactive defense rather than reactive fixes, akin to having a security guard who anticipates trouble before it arrives.
Collaborative Security Features – Strength in Unity
This feature transforms typical security tools into dynamic teamwork environments. Teams can assign security roles, share threat reports, and conduct joint investigations within a secure, isolated workspace. This promotes a shared responsibility model and enhances overall security posture. Unlike others that silo collaboration or complicate workflows, Protection 360™ integrates these aspects seamlessly, making security a shared mission rather than a burdensome chore.
Privacy Control and Data Governance – Your Digital Safe
Managing data privacy has never been easier. The app offers modules where users can set permissions, define encryption levels, and review access history with just a few clicks. Its visual privacy maps display data flow and access points, helping users understand and control where their data is moving—much like managing a digital safe vault that you can oversee at all times. This transparency fosters trust and ensures compliance with privacy regulations.
How Does Protection 360™ Differ from Its Competitors?
While many cybersecurity tools focus purely on individual threat detection, Protection 360™ shines with its integrated collaborative features—making it ideal for teams and businesses that need both security and cooperation. Its unique approach to combining task management with collaborative security workspaces sets it apart. For example, integrating threat reports directly into shared task lists allows teams to address vulnerabilities collectively, drastically reducing resolution times. Additionally, its user-friendly design makes advanced security accessible even to non-experts, which is a significant advantage over complex, technical-heavy solutions.
Final Thoughts: To Use or Not to Use?
Protection 360™ is highly recommended for small to medium-sized organizations and tech-savvy individuals who value both strong security and team collaboration. Its intuitive interface, proactive threat detection, and innovative collaborative features make it not just another security app but a trusted partner for safeguarding digital assets. For those seeking an all-in-one solution that promotes teamwork and enhances security awareness, this app deserves serious consideration.
Similar to This App
Pros
Comprehensive malware protection
Protection 360™ effectively detects and blocks a wide range of malware, including viruses, ransomware, and spyware, ensuring device security.
Real-time monitoring and alerts
The app provides instant notifications about suspicious activities, allowing users to respond promptly.
User-friendly interface
The clean and intuitive UI makes it easy for users to navigate and configure security settings.
Advanced phishing protection
Protection 360™ safeguards against phishing attacks in emails and on websites, enhancing user safety.
Regular automatic updates
The app automatically updates its virus definitions and software to stay ahead of emerging threats.
Cons
Battery consumption may be high (impact: medium)
The app tends to drain battery faster due to continuous background scanning.
Some false positives on benign apps (impact: low)
Protection 360™ occasionally flags safe apps as threats, which can be confusing for users.
Limited free features (impact: medium)
Advanced features such as VPN and identity theft protection require a premium subscription.
Initial setup can be lengthy (impact: low)
The onboarding process involves multiple steps which might be time-consuming for new users.
Performance impact during scans (impact: medium)
Full system scans can temporarily slow down device performance, especially on older devices.
Frequently Asked Questions
How do I get started with Protection 360™ on my device?
Download the app from your app store, open it, and verify your T-Mobile phone number during registration to access all features easily.
Is Protection 360™ free to use?
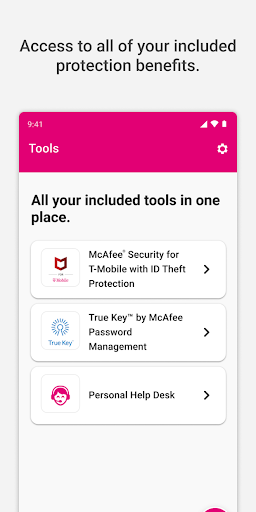
Basic features like tech support and claim filing are included for free with your protection plan. For additional benefits, check your subscription details in Settings > Account > Subscriptions.
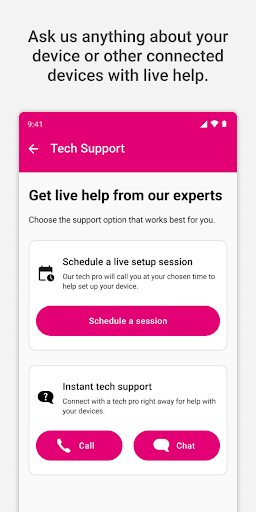
How can I contact live tech support through the app?
Open Protection 360™, tap on 'Support' or 'Chat', and choose to connect via call or chat with an expert, available 7 days a week.
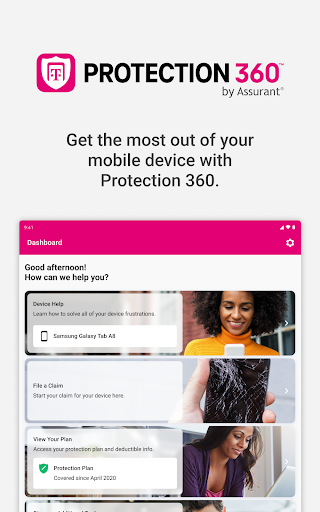
How do I file a claim for damages or device failure?
Go to 'Claims' in the app, then follow the prompts to submit details and upload photos. This process is quick and guided for your convenience.
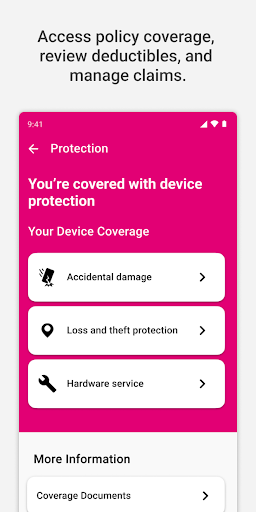
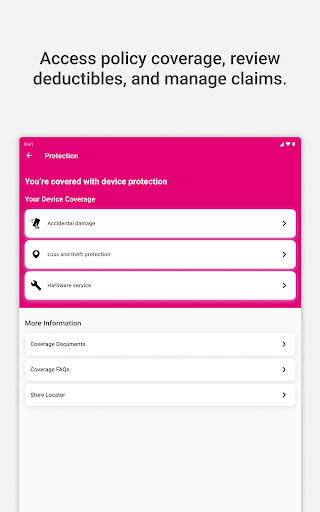
Where can I view my coverage details and FAQ?
Navigate to 'Coverage & FAQ' within the app to see your plan information, deductible details, and frequently asked questions for clarity.
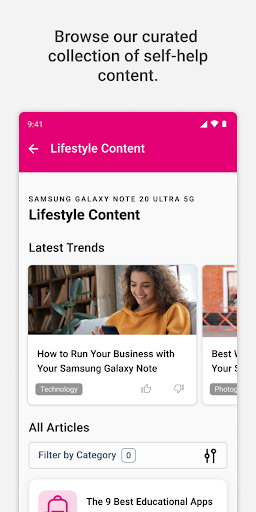
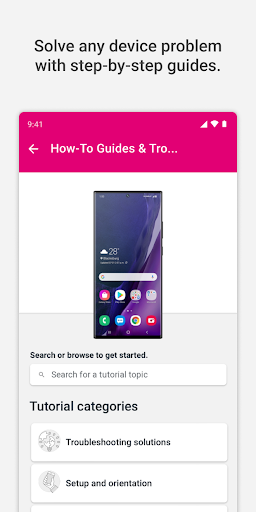
How do I access and use the self-help articles?
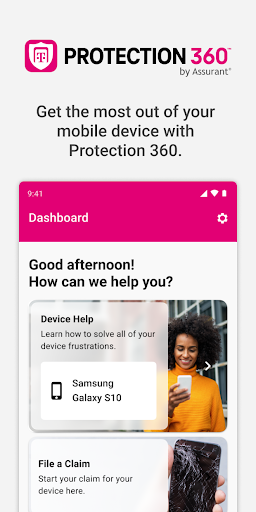
Tap on 'Help Center' in the app menu to browse articles and step-by-step guides that help troubleshoot common device issues independently.
How can I manage my benefits and extras in Protection 360™?
Go to 'Benefits' or 'Extras' in the app menu and verify your eligibility by registering with your T-Mobile number to unlock available services.
How does the security feature scan for threats?
Protection 360™ continuously performs real-time threat detection in the background to identify and neutralize cyber threats automatically.
Can I locate my lost device using Protection 360™?
Yes, go to 'Device Location' in the app to see your device on the map and initiate lock or erase features if needed.
What should I do if the app is not responding or having technical issues?
Try restarting the app, ensure your device is updated, or reinstall it. For persistent problems, contact support via 'Support' in the app.






















